Welcome to our SAP security blog, your go-to source for the latest updates and insights from the ever-evolving SAP security landscape. If you’re navigating the complex realm of SAP systems and their protection, you’re in the right place. Our blog is designed to be your trusted companion on this journey, offering you a treasure trove of insider knowledge straight from the trenches.
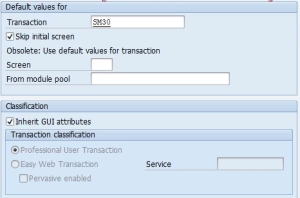
How to create Transactions to display or maintain tables in SAP
In the SAP world, efficiency and simplicity are paramount. One way to achieve this is by creating parameter transactions, also known as parameter transactions. These …
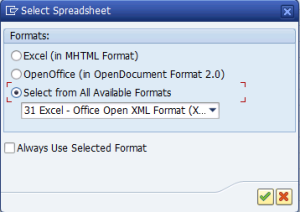
How to Reset the Default Formatting when Exporting to a Spreadsheet in SAP
When you work with reports in SAP and decide to export the data to a spreadsheet, it is common that you want to format the …
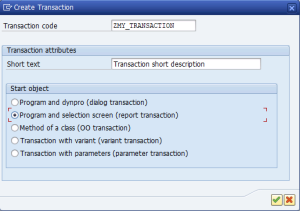
How to create a transaction for a report in SAP
In the SAP world, creating a transaction code for a report is an essential task to facilitate quick access to reports and executable programs. Transaction …
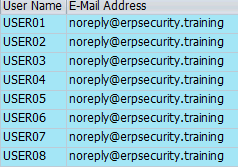
How to Get the List of Users and their Email in SAP
If you are looking for an efficient way to get a list of users and their email addresses in your SAP system, you have come …
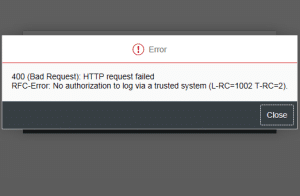
How to Resolve “No authorization to access via a trusted system (L-RC=1002 T-RC=2)” Error in SAP
Attention! If you are an SAP administrator or user facing the annoying authorization error “No authorization to access via trusted system (L-RC=XXXXXX T-RC=X)”, you are …
